Mark Zuckerberg Facebook profile page hacked

Facebook founder and chief executive Mark Zuckerberg has had his profile page hacked by an IT security researcher, after the social network ignored his warnings that a glitch in the site allowed anyone to post on a stranger’s wall.
Khalil Shreateh, a systems information expert from Palestine, attempted to report the vulnerability to Facebook’s security team twice, demonstrating that the glitch was real by posting an Enrique Iglesias video on the wall of one of Zuckerberg’s college friends, Sarah Goodin, with whom he was not connected.
However, Facebook dismissed his warnings, claiming that the issue “was not a bug”, as only Goodin’s friends were able to see the post on her wall.
Frustrated, Shreateh decided to use the glitch to hack into Mark Zuckerberg’s profile page. In a post which has since been removed, he apologised for breaking Zuckerberg’s privacy, adding: “I had no other choice… after all the reports I sent to Facebook team”.
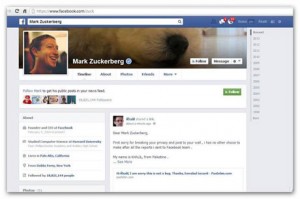
In less than a minute, Shreateh’s Facebook account was suspended and he was contacted by a Facebook security engineer requesting all the details of the exploit.
“Unfortunately your report to our Whitehat system did not have enough technical information for us to take action on it,” the engineer wrote in an email. “We cannot respond to reports which do not contain enough detail to allow us to reproduce an issue.”
Facebook has a policy that it will pay a minimum $500 bounty for any security flaws that a hacker finds. However, the company has refused to pay Shreateh for discovering the vulnerability because his actions violated Facebook’s Terms of Service.
In a Hacker News thread, Matt Jones from Facebook’s security team confirmed that the bug has now been fixed, admitting that the company should have asked more details after Shreateh’s initial report.
“We get hundreds of reports every day. Many of our best reports come from people whose English isn’t great – though this can be challenging, it’s something we work with just fine and we have paid out over $1 million to hundreds of reporters,” he said.
“However, many of the reports we get are nonsense or misguided, and even those (if you enter a password then view-source, you can access the password! When you submit a password, it’s sent in the clear over HTTPS!) provide some modicum of reproduction instructions. We should have pushed back asking for more details here.”
Update: Facebook’s chief security officer Joe Sullivan has responded to this report, outlining changes to the bug submission process as a result of this case. However, Facebook said it would not change its practice of refusing to pay rewards to researchers who have tested vulnerabilities against real users.